What are DoS and DDoS attacks
- WordPress Tutorials
- Updated on

This article will help you better understand what is behind the scenes of a site. In general, all sites are located on different servers. These servers are a kind of computer. When you search for a site address in your browser, these computers display site information after reviewing your request. Each server can support a limited amount of requests, and when the number of logins exceeds the server capacity; These servers are out of reach or so-called down. This is exactly what will happen to your site with DoS and DDoS attacks.
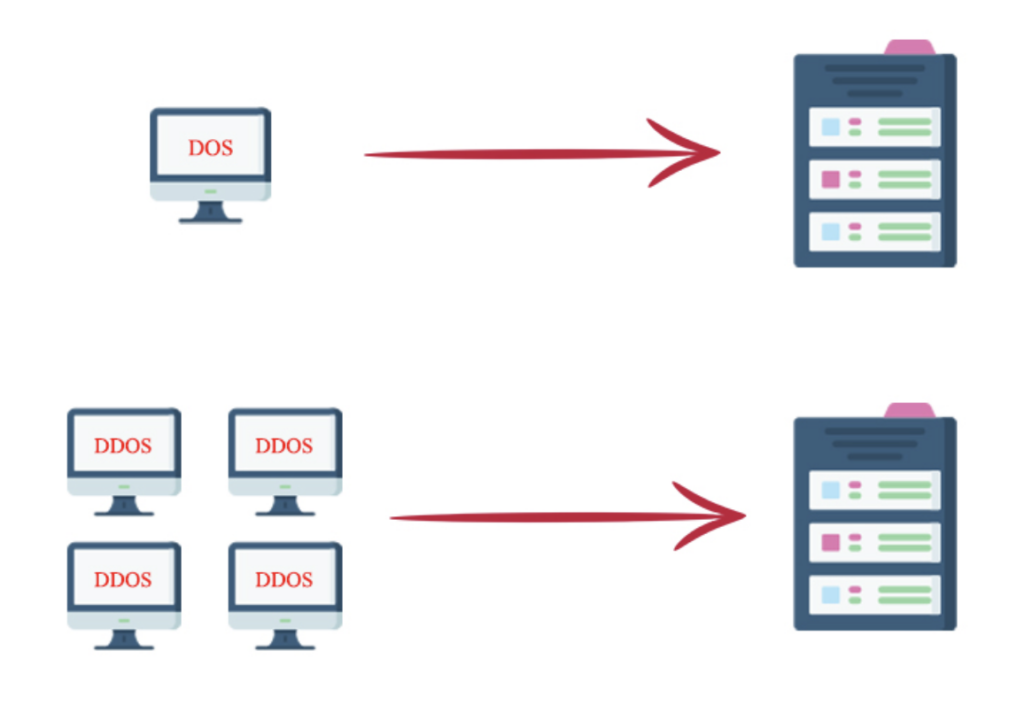
DoS (Denial of Service) attacks are among the most up-to-date and sometimes the most dangerous types of cyberattacks. In this type of attack, hackers try to consume a large amount of site hardware resources by sending a large volume of requests to enter your site, and this movement causes your server to be out of reach for a while.
The primary mechanism of DDoS attacks or Distributed Denial of Service is the same as DoS attacks, except that DoS attacks are performed with one computer. Still, DDoS attacks are carried out through several separate computers simultaneously. Takes.
Generally, these types of attacks occur when abnormal traffic to your site increases and prevents users from accessing your server information. An attacker would block your access to accounts and other services on the system by targeting your computer and its information.
DoS and DDoS attack differences
Given what we have already explained, it is easy to recognize the differences between the two attacks. In DDoS attacks, traffic is diverted to your site from several different systems, making it harder to track and access the attacker and more destructive and widespread than attacks. DOS attacks are generally more straightforward, and you can even attack your target server in a limited size with your system.
attacker
Each individual or group can have its reason for doing so. But there are reports that some of these attacks are carried out to cowardly repel business rivals. Sometimes, people take such information out of reach to destroy some vulgar or anti-social content with such attacks. Of course, some people use these attacks to inform the site administrators about the insecurity of the site against these attacks.
Dos and DDos attack tokens
When these attacks occur, if you find out too soon, you may be able to prevent further damage to some extent. If your server response unexpectedly slows down, it could signify these attacks. But note that sometimes you see these cases, but they are not attacks, but any disruption or even increase of the average user may be.
The next thing is not to connect dynamic pages to the server. In these cases, you will usually receive a message to complete the capacity. It is recommended that you adjust your browsers not to visit your site for a while if you see this. The next sign is an overuse of server resources, such as memory or bandwidth, which usually occurs quickly.
At the beginning of our explanation, we mentioned that attackers try to destroy your server by sending large and unusual requests. If you receive an unusually high number of requests, you should know it is a sign of DOS and DDoS attacks. Sometimes this type of attack targets e-mail or any other services and causes slowing down and disruption in sending and receiving information.
Methods of attack
These attacks have many different methods, some of which we will name for you:
ICMP Flood: In this method, the attacker attacks the target system by sending a request or ping packets and disrupts the service. Repeating this will ultimately occupy the server and disable it.
Teardrop or Teardrop attacks: In this way, the attacker sends the IPs fragmented and incomplete, which naturally causes problems for the recipient’s hardware. Older operating systems, such as Windows 95 are usually more vulnerable to these attacks.
SYN Flood: In this case, the attacker shows himself as a regular user by sending TPC / SYN requests. It then sends its request for information and keeps the server open after receiving a response. By increasing these half requests, the server is occupied, causing the server to crash and eventually crash.
How to prevent Dos attacks
The occurrence of these attacks indicates a defect in the site server. To avoid such problems, you should ask your server administrator to use methods such as the constant updating of hardware and software, the use of firewall programs on systems and servers, the installation of security tools, and so on. If the site administrator knows the amount of traffic and routine requests from the server, they will be notified of the attack as soon as they receive traffic or unusual requests.
It is a good idea to notify your host immediately if you ever see signs of DOS and DDoS attacks to avoid further damage. Sometimes, it becomes tough and impossible to prevent problems after a spell with all these efforts and precautions. Interestingly, the popular GitHub site that all developers are familiar with was exposed to the most significant DDoS attack in 2018. The hackers were able to send about 130 million packets per second.
Duration of the attack
You may be wondering how long it takes from the beginning of the attack to the end. I must say that a definite period cannot be specified for such matters; Because it depends on the stubbornness of the attacker and the strength of the defender. If the attacker continues to work and the defender cannot control the situation well and prevent the attack; The attack may take hours. In the best and most optimistic cases, it ends in a short time (about a few minutes), and in the worst case, these attacks may last for several days and regularly.


To post a comment, please register or log in first.